ForbiddenBITS CTF 2013 WriteUp - poir
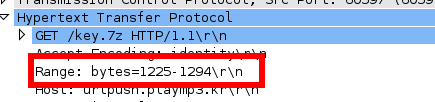
This challenge provides us a file named poir. It is a pcap-ng file. Wireshark shows us more than 10k packages, mostly HTTP traffic. These packages are from the transfer of a file named "key.7z". But this is not only one transfer. This file was send in 500 different pieces, which overlaps and in wrong order.
We use the "Export Objects"-Option from Wireshark to save all 500 pieces. For the next step we have to think about how we can get all files in the right order. We could extract the "Range: bytes="-strings of the poir-file and save those to a new file. If we do this, we can sort the key.7z pieces based on the order of the range strings. Ok, lets do this. 
We write a little python-script which sorts the files and combines them to one file in the one step.
#!/usr/bin/env python
f=open("sort.txt","r")
target=open("res.7z","wb")
c=0
d={}
for l in f:
s= l.split("=")[1]
ss=s.split("-")[0]
d[int(ss)]=c
c+=1
for key,val in d.items():
name="key(%d).7z" % val
print key,val
target.seek(key)
with open(name,"rb") as src:
buf=src.read(1)
while buf:
target.write(buf)
buf=src.read(1)
target.close()
f.close()Now we can extract the files of this archive. There is only one file named "key.png". It is a completely white picture.
We take a close look and see that not all pixels are completely white. We increase the visibility of these pixels.
#!/usr/bin/env python
import Image
image = Image.open('key.png')
new = Image.new('RGB',(image.size))
for x in range(image.size[0]):
for y in range(image.size[1]):
pixel = image.getpixel((x,y))
if pixel == (255,255,255):
new.putpixel((x,y),pixel)
else:
new.putpixel((x,y),(0,0,0))
new.save('key2.png','PNG')The result shows a png with the key.